
In this modern era of instant communication and unstoppable digitalization, it’s no wonder that a smartphone is the tool of choice for our youth when it comes to communicating with others.
Smartphones allow sending instant messages, making calls, and sharing multimedia files with literally anyone in the world, regardless of your location.
In this article, we share four methods to intercept text messages from your kid’s device without violating their privacy and teach you to read text messages from another phone without them knowing hassle-free. All information is also presented in the video version below.
Table Of Contents
Why Someone Might Need to Check My Phone’s Messages?
There are several reasons why someone might want to check your phone’s messages, ranging from legitimate concerns to invasive motives. Here are some common reasons:
- Parental Monitoring
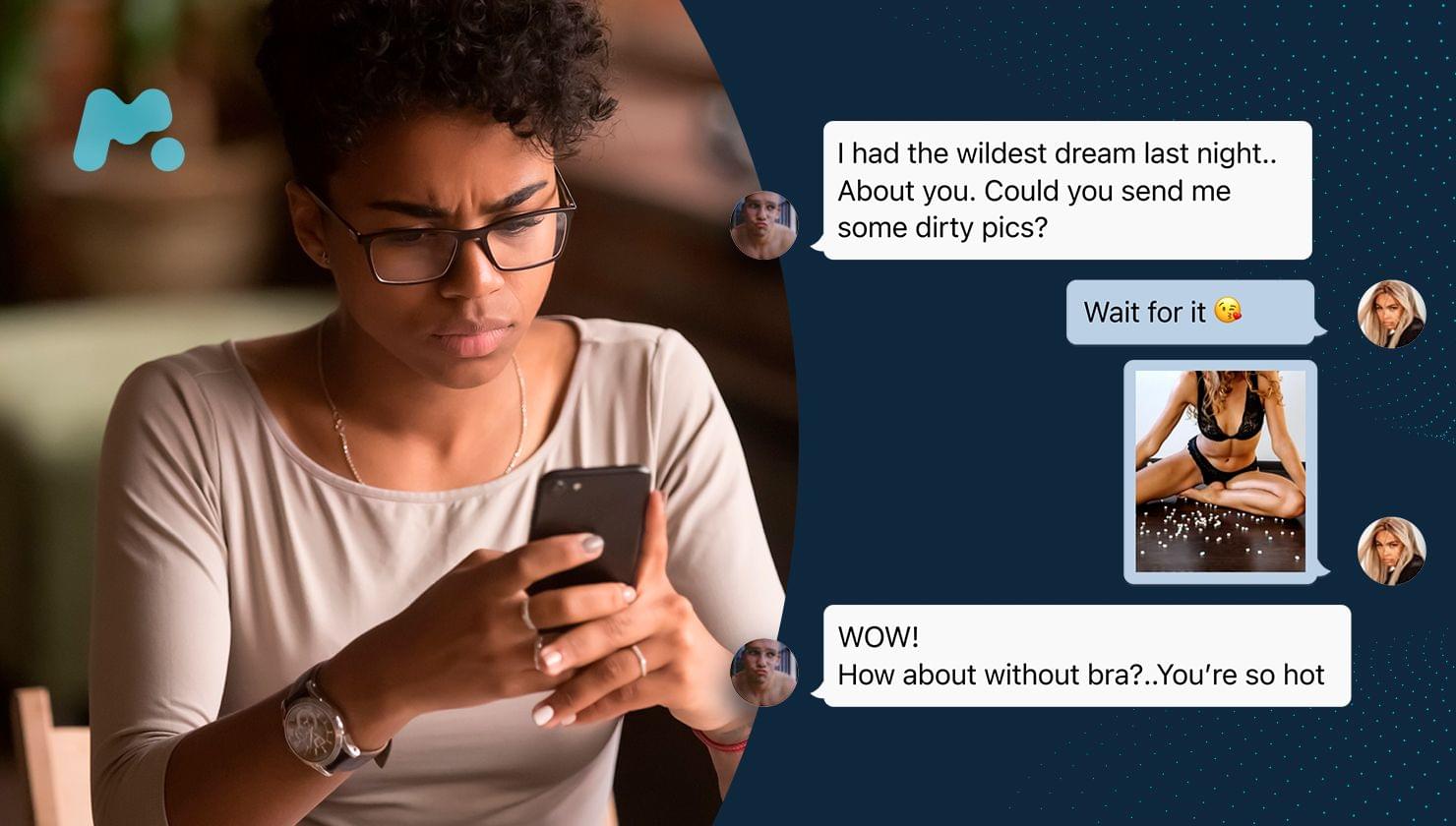
Parents often want to ensure their child’s safety by monitoring text messages. They may check for cyberbullying, inappropriate conversations, or potential online predators. Apps like mSpy or Eyezy allow parents to track messages remotely.
- Suspicious Partner
A partner who suspects infidelity or dishonesty might try to check messages for signs of cheating or secret conversations. This can involve direct snooping or using spy apps.
- Employer Surveillance
Companies sometimes monitor employees’ messages, especially on work devices, to prevent data leaks, insider threats, or inappropriate communication.
- Lost or Stolen Device Recovery
If a phone is lost or stolen, someone might need to check messages for location updates, recovery codes, or emergency contacts.
- Concerned Family Member
In cases of health issues, addiction, or depression, family members might check messages to assess someone’s well-being and provide support.
- Hacking or Identity Theft
Cybercriminals might target messages to steal banking information, two-factor authentication codes, or personal details for fraud.
1. Using mSpy to Track Messages and Chats
Have you noticed that your youngster is depressed? Are all your attempts to find out the source of the problem in vain? Then you should probably think about using parental monitoring software.
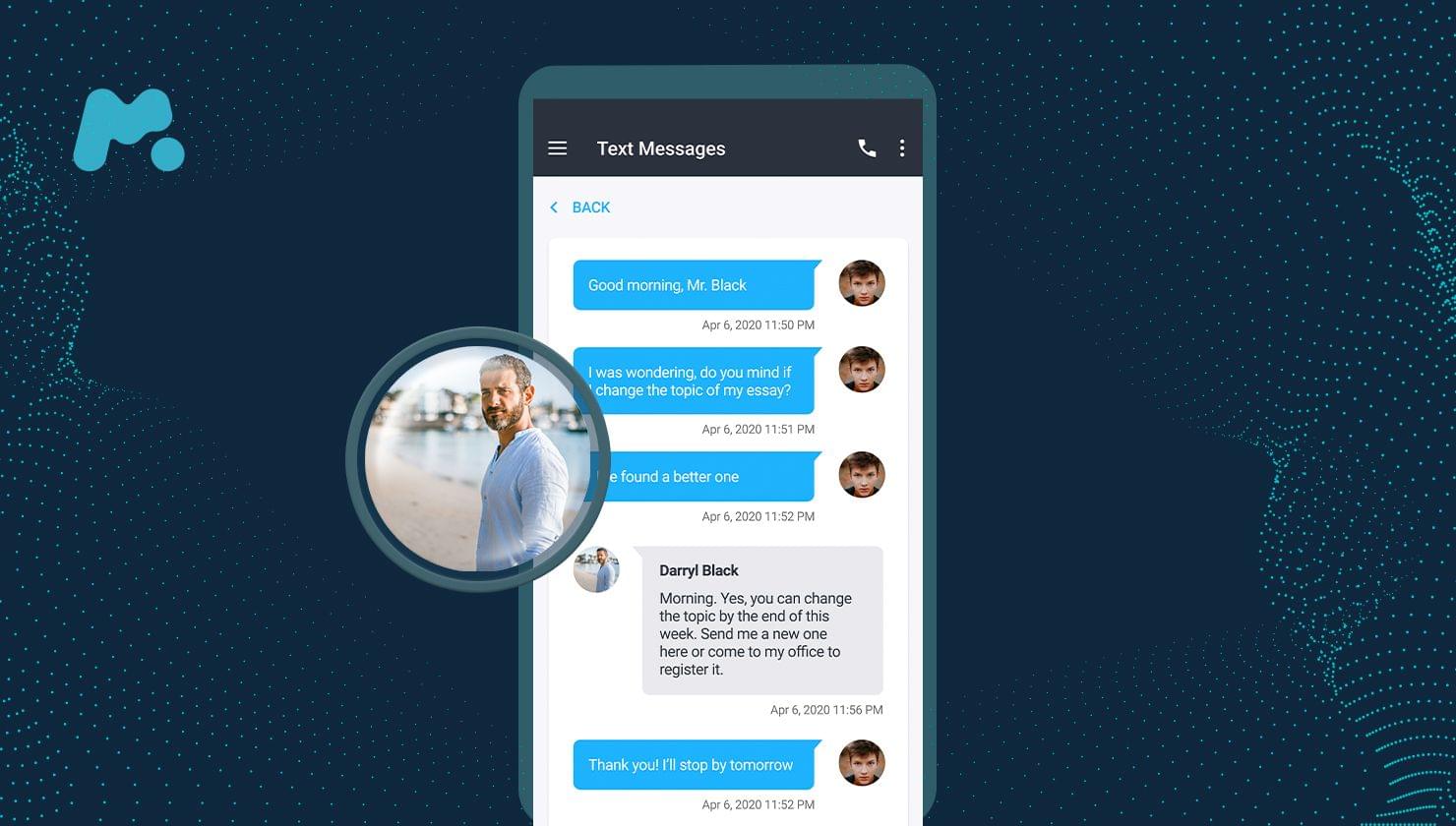
With a parental control app like mSpy, you can easily read someone’s text messages without their phone after you set it all up. To do so, follow a few simple steps:
- Choose a subscription that corresponds to your needs best.
- Fill in the billing information and submit your payment.
- Follow the instructions sent to your email to install mSpy.
- Access your Control Panel and adjust the app’s settings.
- Start reading text messages right from your smartphone.
Note that to install mSpy on an iPhone, you need to use its iCloud credentials. However, setting up the app on an Android device requires installing an apk file.
After completing the installation, you can immediately start to read all text messages on their phone without them knowing, including social media chats and popular messengers, such as Facebook, Snapchat, Kik, and Tinder.
2. Through iCloud or Google Backup
If your iCloud or Google account is linked to your phone, someone with your login credentials can access your text messages remotely. iMessage, Google Messages, and Samsung Cloud allow message syncing, meaning texts may be available from another device.
If someone logs into your backup account, they can read your messages without needing your phone. To prevent this, enable two-factor authentication, use a strong, unique password, and regularly monitor account logins. You can also check your device list in iCloud or Google settings and remove any unauthorized access.
3. SIM Card Cloning

SIM cloning allows someone to create a duplicate of your SIM card, letting them receive your text messages without needing your phone. This method requires access to your SIM card for a short period. Once cloned, the attacker can use another device to intercept your SMS, including verification codes for banking and social media accounts.
To protect yourself, set a SIM PIN code, avoid leaving your phone unattended, and watch for signs like sudden loss of network service. If you suspect SIM cloning, contact your mobile carrier to reset your SIM and block unauthorized use.
4. Using Message Forwarding Features
Some messaging apps allow users to forward text messages to another number or email. If someone gains access to your phone, they can enable SMS forwarding in settings or on iMessage (for Apple devices). This means every message you receive is automatically sent to another device.
To check if message forwarding is active, go to Settings > Messages > Text Message Forwarding on an iPhone or check your messaging app’s settings on Android. Disabling this feature and securing your phone with a strong password can prevent unauthorized access.
5. Using Web-Based Messaging Services
Some messaging services, like Google Messages, WhatsApp Web, or iMessage, allow users to send and receive texts on a computer. If someone gains access to your laptop, tablet, or another device where your messages are synced, they can read your texts without needing your phone.
Attackers can also scan the WhatsApp Web QR code from your phone to mirror your conversations. To prevent this, check for active sessions in your messaging app settings, log out of all unknown devices, and never leave your phone unlocked when unattended.
Can someone read my text messages without my phone?
Yes, it is possible for someone to read your text messages without having your phone. This can happen if your messages are synced to another device, such as a computer or tablet, through services like iCloud, Google Messages, or WhatsApp Web. Additionally, if someone has access to your backup accounts, they can retrieve your messages remotely.
Hackers or cybercriminals can also intercept your texts through phishing scams, spyware, or SIM cloning, allowing them to receive your SMS, including verification codes for banking and social media accounts. Even someone close to you, like a partner or employer, may monitor your messages if they have access to your device credentials or have installed tracking software.
To protect yourself, enable two-factor authentication (2FA), use strong passwords, regularly check for unknown devices connected to your accounts, and avoid clicking suspicious links. Staying vigilant can prevent unauthorized access to your private conversations.


This is a great article and the tips for spotting a cheater or liar are spot on.
Many people who engage in any form of cheating or lying sincerely believe that they’ve not harmed anyone, but that is very seldom the truth. People, relationships, careers and profits are all harmed by these behaviours.
Just say “no”.
Do u have to have targeted phone
Hi, Angis! Yes, if you want to install monitoring software, you need to install it directly on the target device.
Is it really working ?
How do I knownofnitd on my phone? My ex stoled my phone several times. I mean several phones and decided to bring it back 5 days later . I also believe she has a tracker on my phone. Any.help is much appreciated. ainl may have to try later and get her o home to fix it?
What if I don’t have access to their phone my child lives in another state will it still work